Frequently Asked Questions
If you can't find an answer to your question below, please contact support and we'll get back to you.
Errors
Why am I seeing a "The certificate is not valid for the requested usage" error on startup?
This generally happens on older operating systems (Windows XP/2003) that are not connected to the internet and it happens because the root certificates on the machine are out of date since Windows cannot update them automatically.
If you run Directory Monitor as an administrator, the certificate can be installed for you automatically. Use the start menu shortcut "Directory Monitor 2 (Admin)" or the File -> Restart as Admin menu option within the application at least once and it should be able to correct this for you.
If the error persists, you will need to install the root certificate manually. You can download the official required root certificate from Comodo's support site. Install the downloaded certificate to the "Trusted Root" and the error should stop appearing, for instructions on installing a root certificate onto your machine, follow this guide.
When monitoring a Synology server, why aren't any events generated in sub directories?
This issue is a tell-tale sign of Synology's faulty SMB emulator which specifically prevents new subdirectories from participating in real-time monitoring. We've been in contact with Synology but they are reluctant to fix these flaws in their DSM proprietary implementation. The problem was introduced a while ago in version 5.2-5565 of DSM.
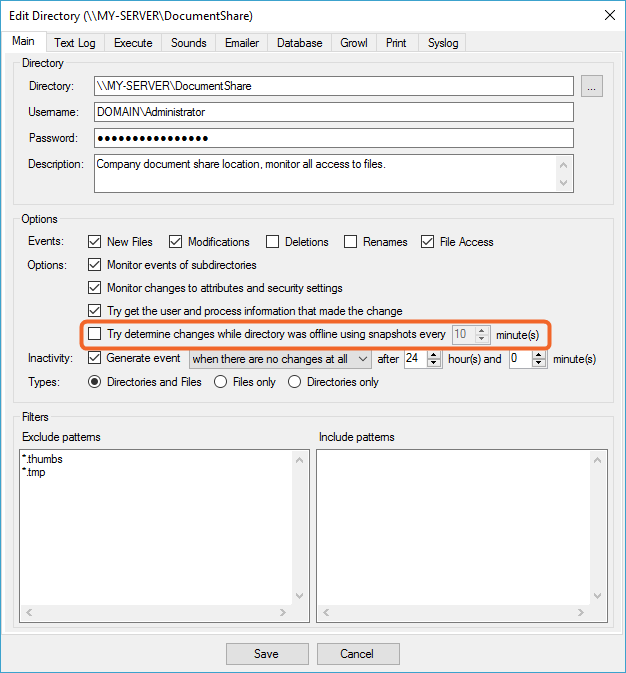
To successfully monitor a share like this, you need to make use of the snapshots feature (which effectively polls for changes). You can enable this option on the problematic share by going to the configuration right-click -> Edit, and enabling the "Try determine changes while directory was offline using snapshots". Use a short interval to recover from real-time monitoring failures earlier and make it more reliable. The drawback is that a lot of disk scanning will occur at the specified intervals so avoid deep and complex directories.
If it was possible to detect the backing operating system of a share we would be able to get the software to warn users of well-known issues like this. Unfortunately there is no open mechanism to query Unix OS details from a Windows machine so it's difficult to know if the SMB implementation is faulty or not. So far, only Synology has this problem of all the Unix operating systems we have tested on.
When applying login details to a share, why do I get warning about "Could not access network share with supplied credentials (1219)"?
This means you are trying to create a network session with two different users accounts to the same share which won't work in Windows.
Looking up the error code in the Windows System Error Codes table, the exact description of error 1219 is "Multiple connections to a server or shared resource by the same user, using more than one user name, are not allowed. Disconnect all previous connections to the server or shared resource and try again.".
Your logged in user probably already has a session to the share you are accessing or you accessed it with another account in Windows Explorer and you are using another account to try and create a second network session in Directory Monitor which Windows does not allow.
You can use the solution mentioned here to clear any existing sessions so that you can create a new one: ServerFault - System Error 1219 Has Occurred
From a command prompt type: net use * /del
User Detection
I have enabled the user detection option, why am I not seeing any user information in the logs?
If you are are trying to monitor a non-Windows share, user detection will simply not be available. There is no way to accurately detect what the backing operating system is through a network share so the feature will simply fail.
If you are struggling to monitor a remote machine it's probably because of strict configuration that is disallowing the monitoring machine to access that sensitive information. To overcome this, you may need to apply certain changes to the target machine to retrieve that data. A Configuration Assistant is provided to make the necessary changes since they cannot be applied remotely, this can be found on the link provided in most of the error messages: WMI Troubleshooting
If you are seeing any errors or warnings in the Activity Log tab, they can also hint at what is causing the problem with user detection failure as well. If all else fails you can send us a problem report (Help -> Report a Problem) so that we can see what your configuration options are and help you determine why this feature is not working.
Why are some of the directory options disabled?
User detection is not available at the drive level, only against directories.
This is a Windows limitation preventing anyone from applying audit settings to a root drive. Audits can only be applied to directories and is more than likely a performance decision, applying full audits at a drive level will certainly bring your disk access down to a crawl because of the number of events that would need to be intercepted and logged by Windows.
The option will be enabled as soon as the path is detected not to be a drive letter or a share backing a root drive.
Unlock Keys
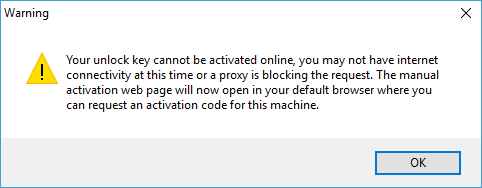
My server/PC is not connected to the internet, how do I activate my unlock key?
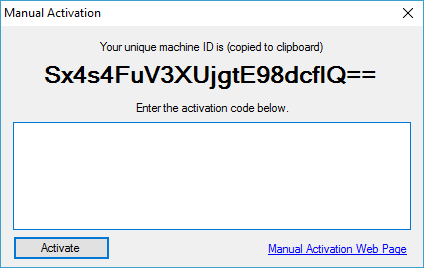
If your unlock key cannot be activated online, you will be presented with an additional dialog to provide the activation code manually. The manual activation page will also open in your default browser with the required fields pre-loaded. Most of the time the browser will be able to access web pages that Directory Monitor cannot.
You can retrieve this code by going to the manual activation page on a machine with internet connectivity and entering your registered email address, unlock key, and machine ID that is displayed on screen. Take the activation code that is generated for you to unlock the features. The activation code will also be emailed to you for your records.
How do I transfer my existing unlock key to another machine?
If you wish to deactivate a machine so that you can make use of the same unlock on another machine (within the limits of your purchase) use the menu option Help -> Deactivate allowing you to re-activate again on another machine. If you are unable to deactivate a machine yourself (lost or inaccessible), you can manually deactivate any active machines with your unlock key information.
Other
Why does my Event Log fill up with "Service command was processed successfully" messages every second?
Exit the user interface when you have the background service option enabled and the "Service command was processed successfully" messages will stop.
These messages cannot be prevented by the application and do not degrade system performance in any way. The Directory Monitor user interface will send heartbeat service commands (every second) to your installed service instance to ensure it does not begin to monitor while the interface is running. This is to ensure reliability as each application takes monitoring responsibility. Those messages are not created by the application so we cannot stop them, they are created by Windows whenever a service command is sent to any service, not only the Directory Monitor service. Closing the user interface, and letting the service take over monitoring responsibility, prevents these messages from being logged.
If you run the service and the user interface simultaneously those messages will appear. The reliability is important as the application should not miss an event so the heartbeat to the service is necessary, but only when the user interface is active.
How can I share the same settings with all users on the same machine?
All users on the same machine can use the provided "Directory Monitor 2 (Shared-User Mode)" shortcut.
This mode is most useful in server environments with several administrators that need to configure and use Directory Monitor. All settings and directory configurations in this mode are not saved against the logged in user's account as it would normally. The service is also stand-alone and does not interfere with any other user instances.
No matter which user you are logged into on the machine with, in shared-user mode the settings will be the same allowing multiple users to configure the same instance of Directory Monitor. An administrator can setup Directory Monitor and it does not run in the context of his or her account.
I would like to translate Directory Monitor, where do I start?
The resource files are in RESX format so you can use any compatible editor to generate a new resource file for German and translate the strings side-by-side. The best free one in my opinion is Zeta Resource Editor. The new resources will be imported and the necessary user interface adjustments made to fit everything in, you'll get a new build to try out and verify before going live.
Download the resource strings here: String Resources
I would like to become a Directory Monitor reseller, where do I sign up?
By default we offer a 10% discount to new resellers. If the reseller provides some other service (translated site or software, new revenue stream etc) then the discount will be more. The discount amount increases for sales made, you can decide if you want to offer this discount to your customers or keep the saving for yourself to make a profit.
You can take a look at the discount tables here: Reseller Portal
Contact support and we can create a login for you to access the reseller portal.