WMI Troubleshooting
User detection against remote machines (network shares) requires specific permissions on the target machine to allow Directory Monitor to access the user information over WMI.
Object Auditing Error
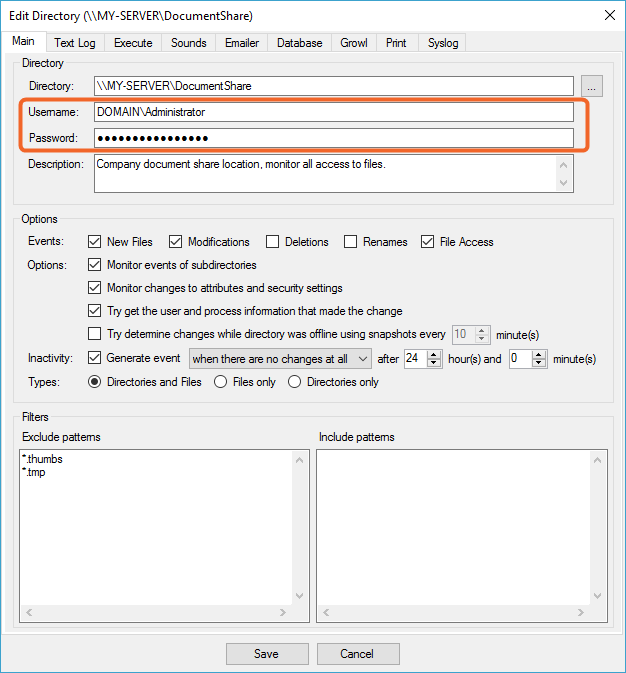
If remote configuration settings cannot be applied, the directory will typically have a warning symbol next it and you see the following warning when trying to save your configuration.
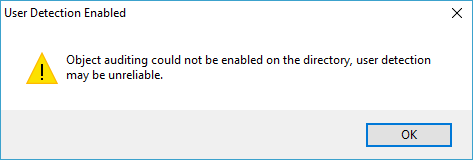
When monitoring local drives and directories, Directory Monitor can configure the machine appropriately for user detection. This complex configuration cannot be applied remotely over the network so a separate configuration tool is provided.
This can also happen if you are trying to audit a machine that is not running Windows (Unix NAS for example). User detection only works against Windows machines, Unix does not provide the tracking facilities necessary to know who is making changes.
User credentials cannot be used for local connections
You may see this error if you are trying to monitor a share that exists on the local machine running Directory Monitor. Instead of monitoring the share, simply monitor the local drive path that your share points to and you will not require credentials.
Configuration Assistant
We provide a remote machine configuration assistant to easily apply the necessary settings on the target machine for successful remote user detection.
If the network share you want to monitor is \\MYSERVER\myshare, you need to run the configuration assistant on MYSERVER.
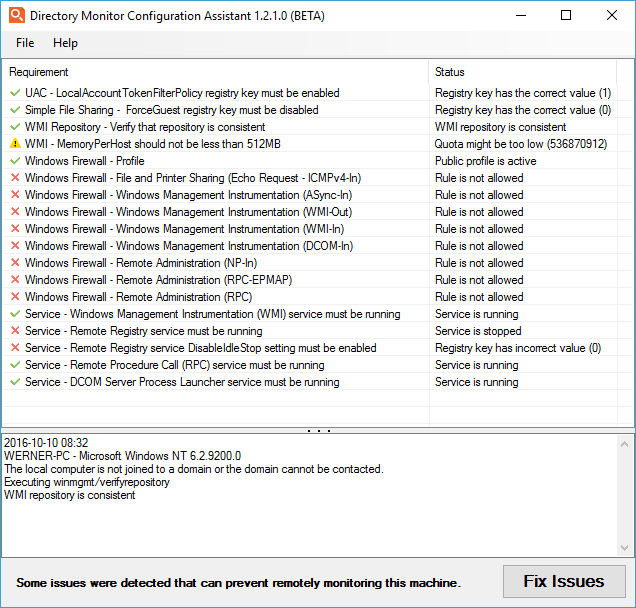
Let the configuration assistant detect the potential problems the target machine may have and try to fix them automatically. After applying the settings, go back to the machine running Directory Monitor, edit the target network share and save the settings again to re-apply them to the share.
Administrator Privileges
The configuration assistant requires administrator privileges to automatically apply the settings required for remote monitoring. Ensure you login to to the target machine as a local or domain administrator capable of making these changes. If you do not have sufficient access rights to make the changes, you simply do not have sufficient rights to view the user information on a machine you do not own.
To access and view user information over the network, you also need to be an administrator on the target machine. If you are not logged in as a domain administrator with sufficient access to the target, you will need to provide a username and password to create an elevated network session on the target capable of reading this secure information.